Understanding SQL Injection Attacks
SQL injection (SQLi) is a technique used to inject malicious code into existing SQL statements.
These injections make it possible for malicious users to bypass existing security controls and gain unauthorized access to obtain, modify, and extract data, including customer records, intellectual property, or personal information. Attackers can also use this technique to locate the credentials of administrators and gain complete control over affected websites, applications, and database servers.
SQL injection attacks can affect any application that uses a SQL database and handles data, including websites, desktops, and phone apps—with extremely serious consequences.
How Does SQL Injection Work?
SQL injections are typically performed via web page or application input. These input forms are often found in features like search boxes, form fields, and URL parameters.
To perform an SQL injection attack, bad actors need to identify vulnerabilities within a web page or application. After locating a target, attackers create malicious payloads and send their input content to execute malicious commands.
In some cases, bad actors may simply leverage an automated program to carry out an SQLi for them—all they need to provide is the URL of the target website to obtain stolen data from the victim.
Types of SQL Injection Attacks
Injections were listed as the number one threat to web application security in the OWASP Top 10, and SQL injection vulnerabilities can be exploited in a variety of different ways.
A few common methods for SQL injections include executing commands on the database server, retrieving data based on errors, or interfering with the query logic.
Union-Based SQL Injection
This type of SQL injection is the most popular method performed by attackers.
This injection technique allows bad actors to extract data from the database by extending the results from the original query. It uses the UNION SQL operator to integrate two SELECT statements into a single result, then returns it as part of the response.
Blind SQL Injection
Typically more sophisticated and difficult to perform than other varieties of injections, attackers perform blind SQL injections when generic error messages are received from the target.
Blind SQL injections differentiate themselves from regular SQL injections in the method that they retrieve information from the database. In this technique, bad actors query the database for true or false questions, then determine the answer based on the response, as well as the time it takes to retrieve a server response when using it with time-based attacks.
Boolean-Based SQL Injection
This type of attack overwrites the logic and conditions of the query to its own. It is commonly used in permission or authentication queries, where they trick the database into thinking they have elevated permissions or correct credentials.
Boolean-based SQL injections are also used in blind SQL injections, where they proceed by elimination to extract data from the database. By sending tons of requests, each with a condition slightly different from the precedents, attackers can figure out what is the data stored based on the result of the operation.
Error-Based SQL Injection
In an error based SQL injection, attackers exploit database errors from a web page or application that have been triggered by unsanitized inputs.
During an attack, this technique uses error messages to return full query results and reveal confidential information from the database. This method can also be used to identify if a website or web application is vulnerable and obtain additional information to restructure malicious queries.
Time-Based SQL Injection
During a normal SQL injection, bad actors can simply read text as it is returned. However, when attackers are unable to retrieve information from a database server, they will often employ time-based SQL injections to achieve their results. This works by using operations which take a long time to complete—often many seconds.
Time-based SQL injections are commonly used when determining if vulnerabilities are present on a web application or website, as well as in conjunction with Boolean-based techniques during Blind SQL injections.
SQL Injection Example
In the following SQL injection example, we try to login by comparing the user input (username and password) to those stored in the database.
This is an example of what NOT to do—this query has multiple flaws by design. Notably, it is vulnerable to SQL injection, and does not use hashed and salted passwords.
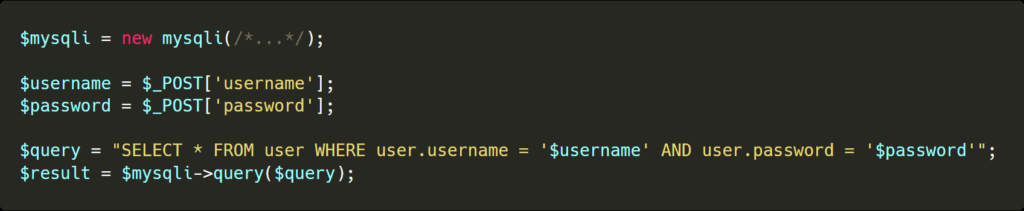
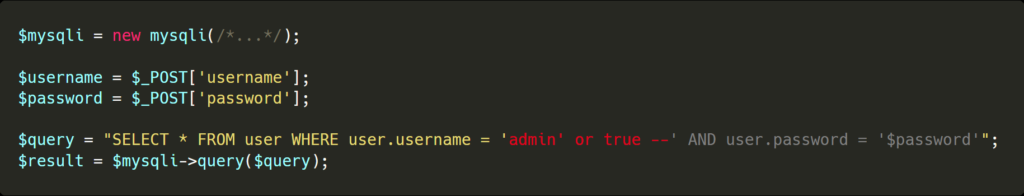
In this example, the query is built by concatenating the user-specified values (username and password) directly into the query.
This makes it easy for an attacker to escape the quotes and inject more SQL operations. By having the following username admin’ or true — it is possible for an attacker to login with the account of his choice.
How to Detect an SQL Injection
SQL injections are notoriously difficult to detect. Unlike cross-site scripting, remote code injection, and other types of infections, SQL injections are vulnerabilities that do not leave traces on the server. Instead, the exploit executes genuine queries on the database. As a result, the majority of attacks are detected once an attacker has used a vulnerability to perform malicious actions or gained administrative access.
By taking precautionary measures and actively monitoring your database and its queries, you can identify if an attacker is running malicious injections on your website.
How to Prevent SQL Injection Attacks
Attackers frequently target websites that use known vulnerabilities. Undisclosed, unpatched, or zero-day vulnerabilities also account for a large percentage of SQL injections during targeted attacks.
The easiest way to protect your website against SQL injections is to keep all of your third party software and components up to date. However, a number of techniques exist that you can use to help prevent SQL injection vulnerabilities.
Use Prepared Statements with Parameterized Queries
Prepared statements are used to ensure none of the dynamic variables you need in a query can escape their position. The core query is defined beforehand, with the arguments and their types afterward.
Since the query knows the type of data that is expected, such as string or number, they know exactly how to integrate them to the query without causing issues.
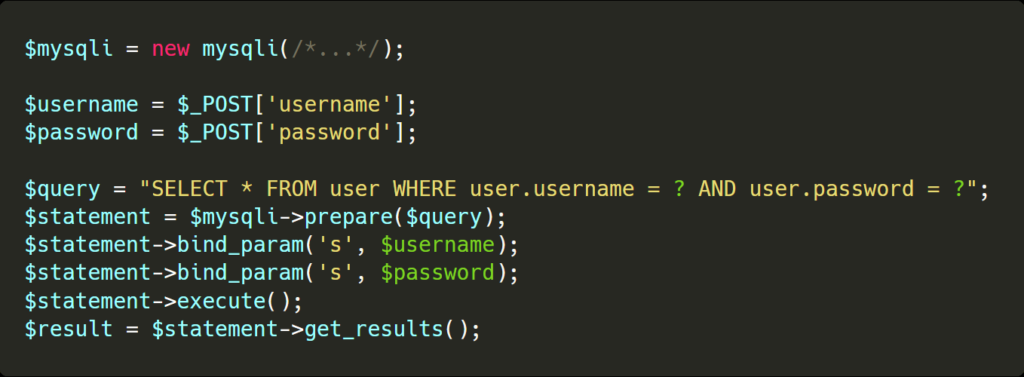
In this example, even if the username or password variables attempt to escape their query, the prepared statements properly escape their characters to prevent unexpected behavior or SQLi.
Use Stored Procedures
Stored procedures are frequent SQL operations that are stored on the database itself, varying only with their arguments. Stored procedures make it much more difficult for attackers to execute their malicious SQL, as it is unable to be dynamically inserted within queries.
Whitelist Input Validation
As a rule of thumb, don’t trust user-submitted data. You can perform whitelist validation to test user input against an existing set of known, approved, and defined input. Whenever data is received that doesn’t meet the assigned values, it is rejected—protecting the application or website from malicious SQL injections in the process.
Enforce the Principle of Least Privilege
The Principle of Least Privilege is a computer science principle that strengthens access controls to your website to mitigate security threats.
To implement this principle and defend against SQL injections:
- Use the minimum set of privileges on your systems to perform an actions.
- Grant privileges only for the time that the action is necessary.
- Do not assign admin type access rights to application accounts.
- Minimize the privileges to every database account in your environment.
Escape User Supplied Input
During a normal SQL injection, bad actors can simply read text as it is returned. However, when attackers are unable to retrieve information from a database server, they will often employ time-based SQL injections to achieve their results. This works by using operations which take a long time to complete—often many seconds.
Time-based SQL injections are commonly used when determining if vulnerabilities are present on a web application or website, as well as in conjunction with Boolean-based techniques during Blind SQL injections.
Use a Web Application Firewall
You can protect against generic SQL injections with a web application firewall. By filtering potentially dangerous web requests, web application firewalls can catch and prevent SQL injections.
What To Do If Your Website Has Been Hacked by SQL Injection
In the event of a SQL injection, there are a number of steps you can take to fix your website.
Locate the Vulnerable Code
The first step in recovering from a SQL injection attack is to identify where the vulnerability is located. You can manually launch an attack or run an automated SQL injection attack tool like Havij, SQLmap, or jSQL to identify vulnerable code.
Remove Injected Content and Backdoors
Once you have obtained information about the location of the malware, remove the malicious injections and bad data from your database and restore it to a clean state. You’ll also want to check the rest of your website and file systems for backdoors.
Patch the Vulnerability
Vulnerabilities in databases, applications, and third-party components are frequently exploited by hackers. Once you have identified the vulnerable software, apply patches and updates to the vulnerable code along with any other out-of-date components.
Update Your Data
When a compromise occurs, it is important to change all of your passwords and application secrets as soon as the vulnerability is patched. Prevent reinfection by cleaning up your data to ensure that there are no rogue admin users or backdoors present in the database.
SQL Statements
Set up a monitor to identify any rogue SQL statements to your database. A tool that uses behavioral analysis and/or machine learning can help detect indicators of compromise (IoC) to your website.
Set Up a WAF
Consider setting up a web application firewall to filter malicious requests to your website. These can be particularly useful to provide protection against new vulnerabilities before patches are made available.

